A couple weeks ago, I participated in the Magnet Virtual Summit 2025 CTF (Capture the Flag). While I don’t think I will ever see a day where I win one of these, (speed is not my forte), I enjoyed working through a good number of the challenges, starting with the lower point values and working my way up. The CTF covered images/sources including: Cipher challenges, iOS and Android full file system images, Google takeouts, and images of a Windows 11 workstation and a Chromebook. I spent my available time working on the iOS and Windows challenges. I wasn’t able to complete all of them, but I’ll share what I was able to complete.
In this post I’ll be sharing my solutions for the iOS challenges. Warning: SPOILERS AHEAD!

To determine the version of iOS, I used the iLEAPP report for the device.

Another way of finding this information in Axiom is to review the Powerlog Battery Shutdown events.
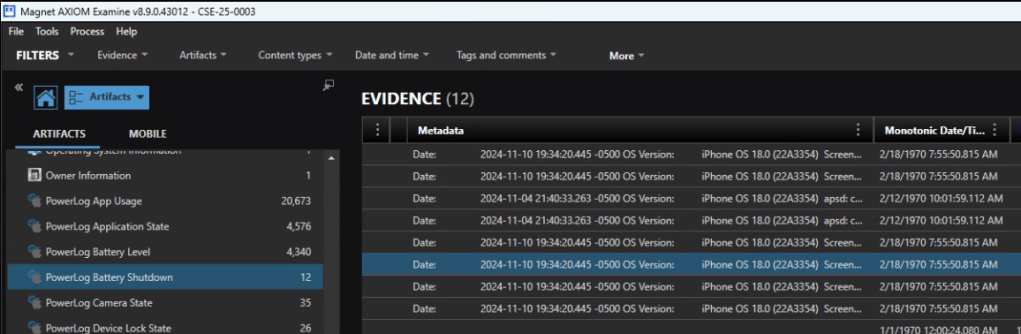
The answer is 18.0

Looking at the Owner information in Axiom is quick way to identify the telephone number associated with the device. 18024959063.


For this one you could start in Contacts or start with a Date/Time filter as that was very specific to the question. The answer is Mary.


Reviewing the iOS Call Logs in Axiom we see that the user never answers their phone. (I can relate.) The answer is “0”.


That’s a ducking odd thing to be curious about. According the the Keyboard Usage Stats, the answer is 51.

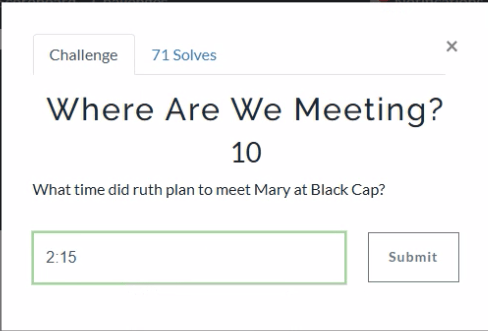
In a Discord chat, Mary and Ruth agree to meet up at 2:15 for coffee.


Started off with a global search on ‘bitmoji’ and then reviewed the media files. (Brown)

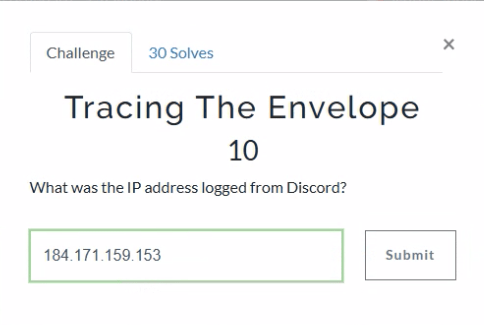
A global search on Discord narrows the results. There is an apple mail message from Discord about the user signing in from a new location. The IP address is 184.171.159.153.


Ah, Nashville. Home of the Magnet User Summit coming up in just a few weeks. iLEAPP can provide us with the Lat and Long of the cities configured in the Weather app.

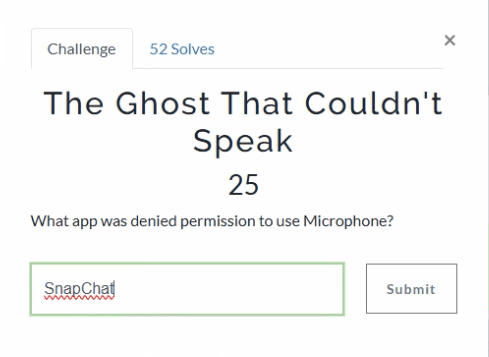
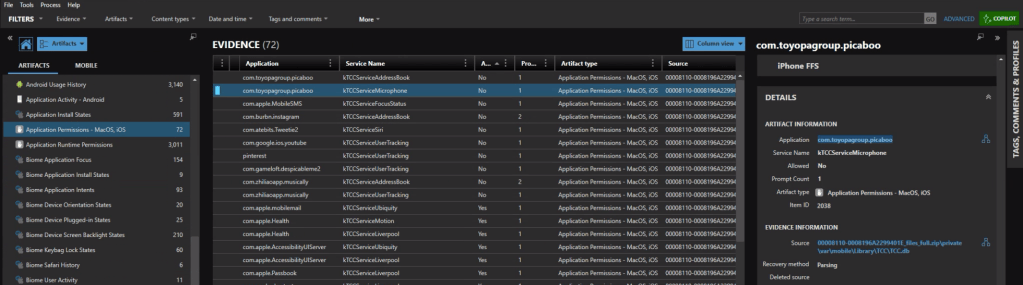
Looking at the Application Permission we can see which applications had (or were denied) access to the microphone. The app identifier com.toyopagroup.picaboo corresponds to Snapchat. The name “Picaboo” refers to Snapchat’s original name before it was rebranded.

In the iOS Messages, we find a number of ‘sale’ announcement from Zenni. EARLYBF24 is the code associated with the 40% off promotion.


First off, we need to know what TikTok video this is referring to. In the iOS messages we see a TikTok video that was shared.

Copy the url and head over to Ryan Benson’s Unfurl. Unfurl decodes the different elements of the url string. One of the details embedded in the string is the time the video was posted. 2024-11-12 22:11:09.

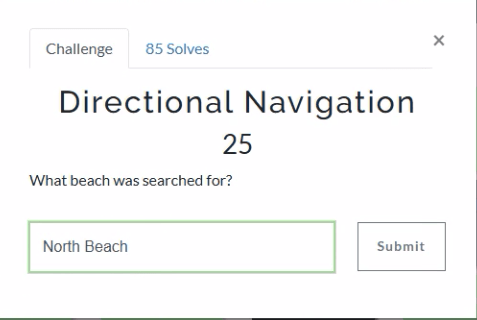
For this one we can take a look at the Apple Maps – Biome App Intents, and see a search for directions to North Beach Park.


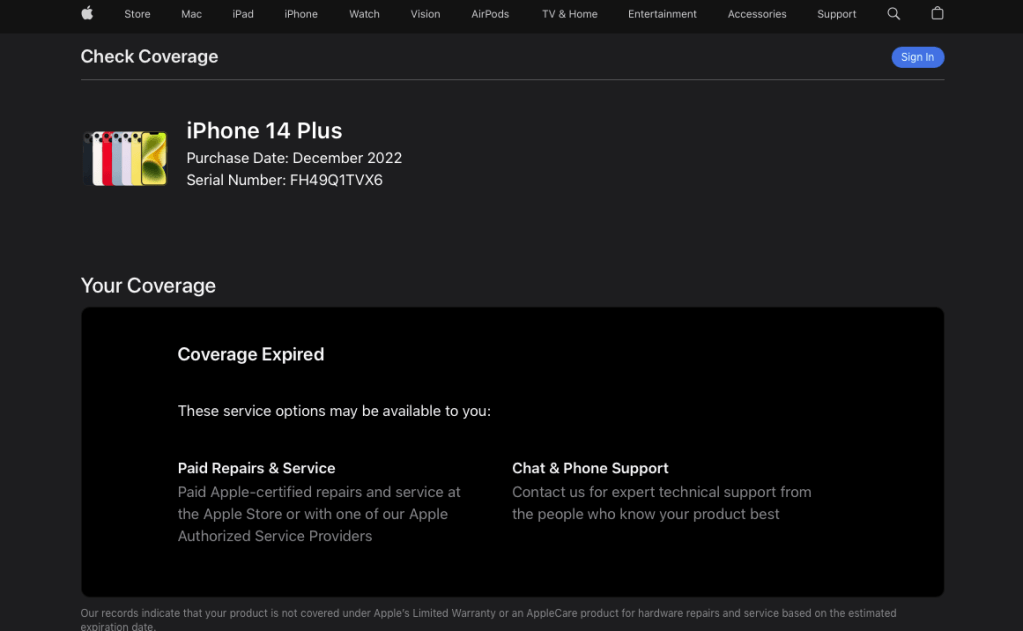
When I first looked at this one I thought there could be a “Welcome to your new iPhone” message or something similar. No dice. Besides, that would be too easy for a 25 pointer. A quick googling indicated was that one way to confirm the purchase date of an iPhone is too look up the warranty status on checkcoverage.apple.com.
We can grab the serial number for the device from iLEAPP.

Plugging that into the warranty coverage site we get: December 2022 (2022-12).
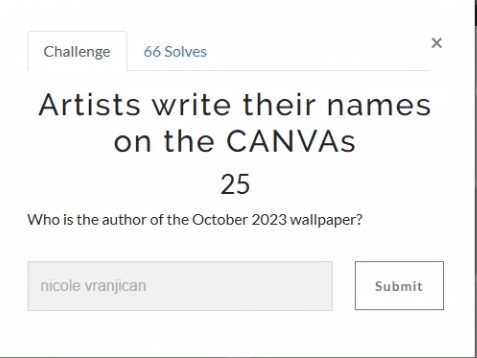
“October” is a good search to start with. Within the PDF documents we find a reference for an October-2023-iphone-wallpaper. In the details we see that the author of this image was nicole vranjican.

There were a few more higher point challenges in the iOS section, but that’s as far as I made it in the allotted time. I’m looking forward to reading other’s write-ups, both for the questions I was unable to solve, as well as seeing the unique and alternative ways that others solved the ones I did.
Stay tuned for my next post on the solutions for the Windows challenges.
If you’d like to access the images used for the CFT for your own training and investigation, you can find them at https://cfreds.nist.gov/all/Hexordia/2025MVSCTF.
Last but not least, my heartfelt appreciation to the team at Hexordia who put together the CTF. Another PUNderful job!
















