You know how these things go. A colleague asks a simple question, and before you know it, you’re knee-deep in PowerShell creating something that didn’t exist a few weeks ago. That’s exactly how CyberPipe-Timeliner came to be.
After a recent update to CyberPipe, someone asked whether there was a way to pipe Magnet Response collections through to something like ForensicTimeliner. It was one of those “that should exist” moments. So I made it exist.
A Quick History Lesson

For those who haven’t been following along, CyberPipe (formerly CSIRT-Collect) has been around since my IR days. It went public in 2021 and has been steadily maintained and updated since then. The tool has proven itself useful for rapid incident response collection, and it’s evolved based on real-world needs and feedback from the community.
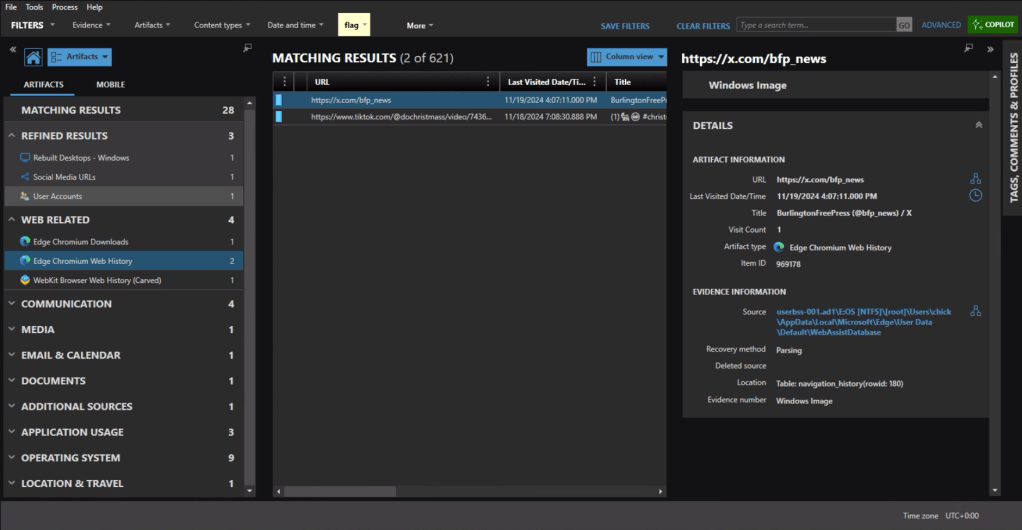
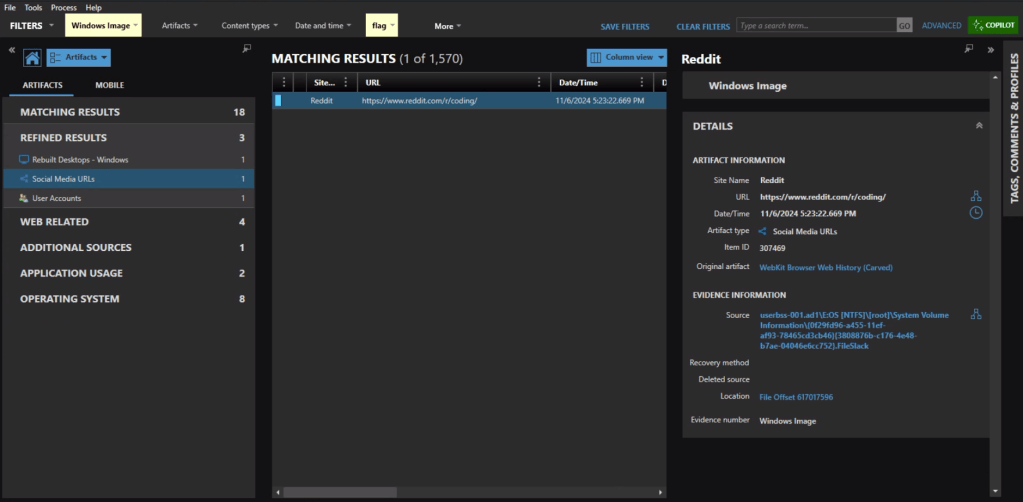
CyberPipe-Timeliner is its companion project—taking that collection data and turning it into something immediately actionable: a unified forensic timeline.
What It Actually Does
The script automates the entire workflow from collection to timeline:
Extraction – It unpacks your Magnet Response archive, whether that’s a ZIP file or an already-extracted directory.
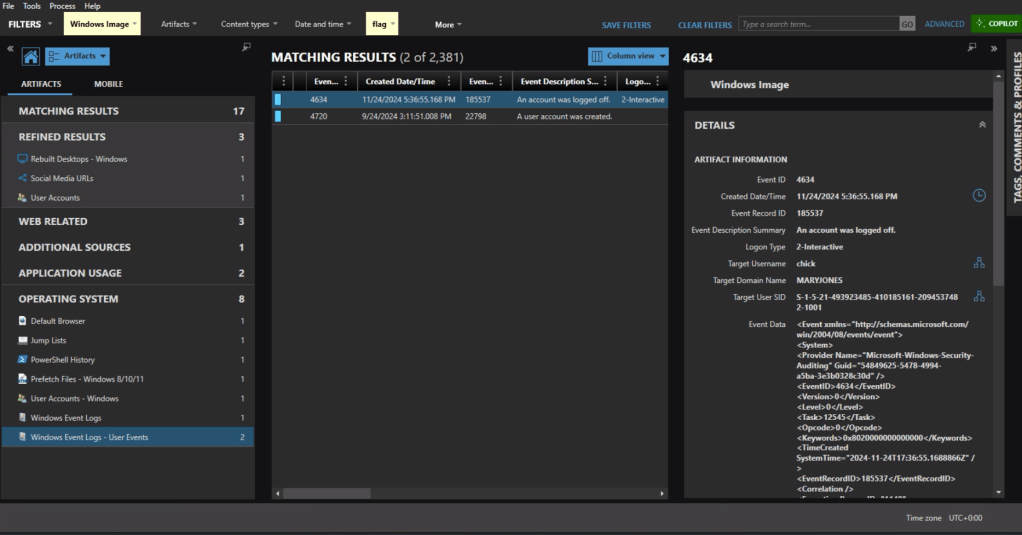
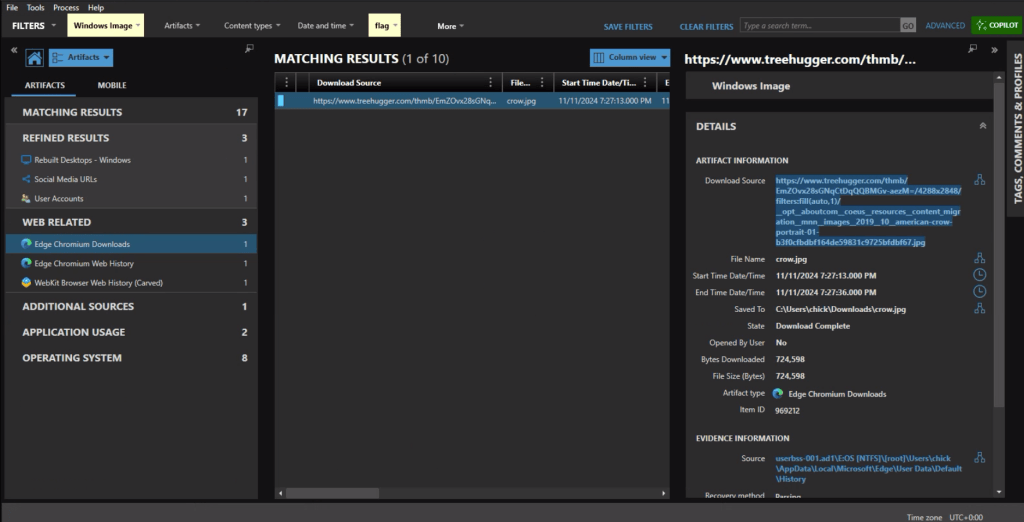
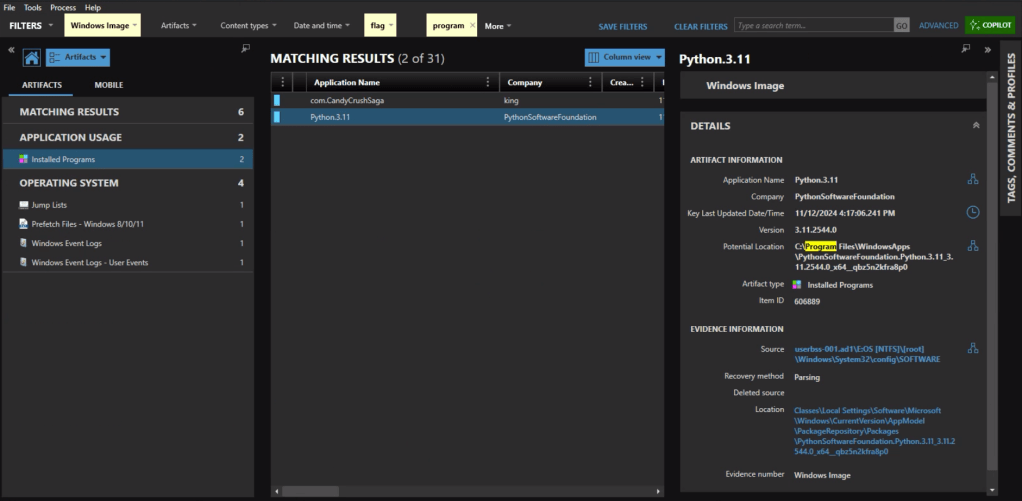
Processing – All the heavy lifting happens here using Eric Zimmerman’s EZ Tools to generate CSVs from your artifacts.
Organization – The CSVs get structured specifically for ForensicTimeliner compatibility, because nobody wants to spend time wrestling with file formats.
Aggregation – Everything merges into a consolidated timeline, giving you that unified view we’re all after.

Built for Real-World Use
The script includes some practical features that came from actual use cases:
- Date filtering – Need to focus on a specific incident window? Use
-StartDateand-EndDateto narrow your timeline to what matters. - Flexible input – Point it at a ZIP file or an already-extracted collection folder. Either works.
- Verbose and diagnostic modes – Because sometimes you need to see exactly what’s happening under the hood.
- Auto-generated output folders – Timestamped folders keep your timelines organized without any extra effort.
Getting Started
Setting it up is straightforward. You’ll need PowerShell 7+, Eric Zimmerman’s EZ Tools, ForensicTimeliner, and Microsoft .NET SDK (v9 recommended). The GitHub repository has detailed setup instructions, including handy one-liners for downloading and configuring the required tools.
Once you’re set up, a basic run looks like this:
.\CyberPipe-Timeliner.ps1 -InputFile "collection.zip"
That’s it. The script handles the rest, creating a timestamped output folder with your complete timeline.
Why It Matters
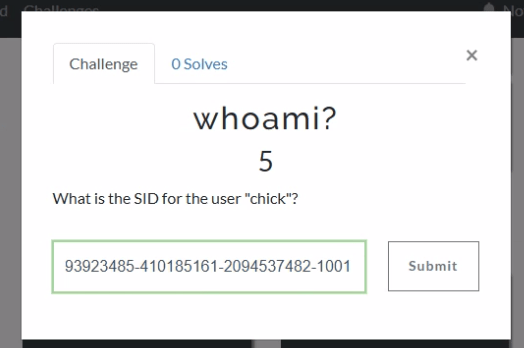
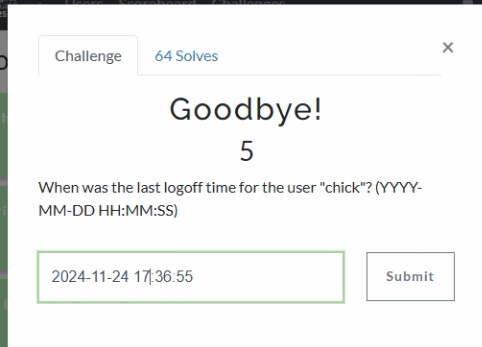
Forensic timeline generation shouldn’t be a multi-tool, multi-step headache. CyberPipe-Timeliner takes what would normally be several manual processes and condenses them into a single automated pipeline. You collect with Magnet Response or CyberPipe, run the timeliner script, and get actionable timeline data.
It’s available now on GitHub, and as always, feedback and contributions are welcome. If you run into issues or have ideas for improvements, open an issue or reach out.
Sometimes the best tools come from simple questions and the willingness to build the answer.