I’ve been participating in the MAGNET sponsored Capture the Flag (CTF) events since before being happily employed there. In a way you could say that one helped facilitate the other, but that’s a story for another time. This blog actually started back in 2020 to, among other things, share my write-ups of that years CTF.

The 2024 CTF event was part of the Virtual Summit that ran from February 27th to March 7th. There were more than 50 presentations about topics like mobile forensics, artificial intelligence, eDiscovery, malware, ransomware, digital evidence review, video forensics, and live Q&A sessions.
If you missed my talk on Investigating Malware With Free Tools and Magnet AXIOM Cyber, you can now watch that and all the other recordings at the 2024 Replays site.
The CTF questions were divided into three groups, iOS, Android & Ciphers. The evidence sources included a full file system extraction of an iPhone 14, a logical extraction of an Android phone, a Facebook ‘Download Your Data’ export and an export of Discord messages. I focused almost entirely on the iOS questions, and even had a few of those left on the table when the 3 hours allotted for the challenge was up. The numbers in parenthesis represent the point value which is intended to align to question difficulty. I processed the iOS extraction with AXIOM Cyber and iLEAPP.
MVS 2024 CTF: iOS
Why are your messages green? (5)
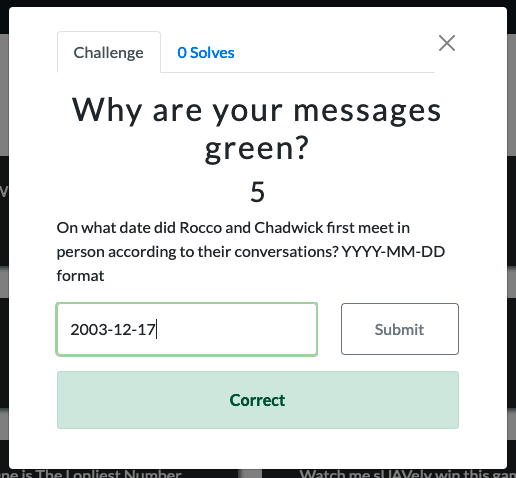
For this one we’ll use MAGNET Axiom, specifically the Conversation View. In the message thread below, we can determine from the conversation that the first time the two persons met was December 17, 2003.

Where /r u going on Safari? (5)

Examining the users Safari history we see that the user visited the url https://www.reddit.com/r/Twitch

IMAGEine living in pain (5)

The question title suggests (not so surreptitiously) that we’re going to be dealing with an image file. In the MEDIA > Photos Media Information we see a picture of a store shelf of a pain relief gel. (I know the feeling. Take care of yourself young forensicators; and don’t forget the sunscreen.) The price of the item was $10.99.

Answer the call (5)

In the Refined Results for Web Chat URLs we see the user visiting a Discord server with the guild ID of 136986169563938816.

Don’t ghost me (5)

To solve this one we’re first going to need to know what MYAI refers to. Running a global search for MYAI shows that it’s a SnapChat “Artificial Intelligence” bot. Again we’ll switch to Conversation View. Once we do so we can see that Chadwick was annoyed with MYAI on December 26th at 11:27:45 UTC.

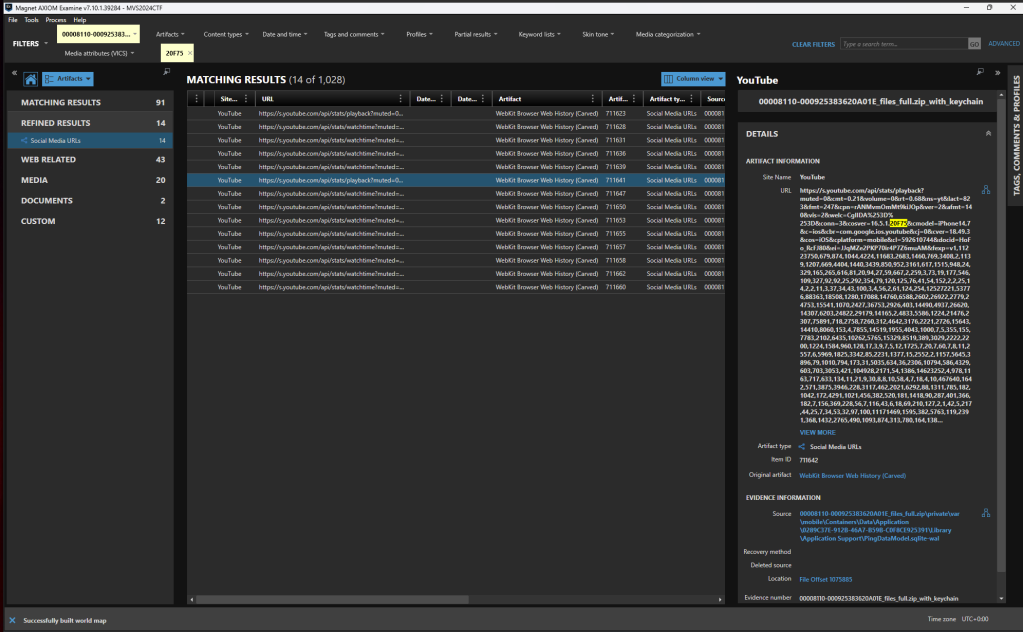
Build me up, buttercup (5)
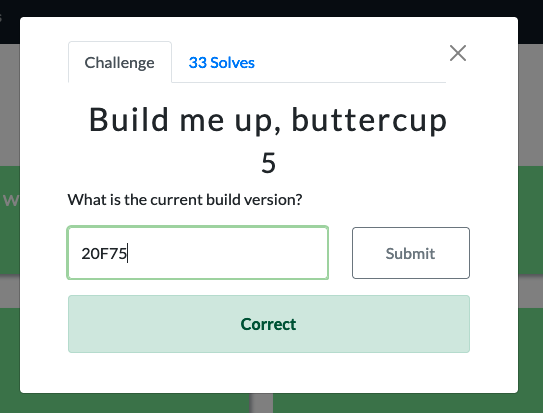
For this question I found it easier to produce the result from the iLEAPP report. What I found interesting is identifying all the other locations where the build ID of the device may be captured, like in the user’s YouTube playback history.

Warning Signs (5)

In order to get this flag we need to combine two iOS iMessage events. We see that the user joined Boost Mobile on November 29th. The warning about reaching maximum data usage was received on December 27. There are 18 days between those dates.


One is The Loneliest Number (10)

The answer for this one can be found in the iOS snapshots on the device. This is often an interesting artifact for me as you get a glimpse (literally) into the applications that have been used on the device. These snapshot images are recorded whenever a user switches between one application and another, and is what produces the carousel like view when switching apps. It looks like Chad’s feeling a little short on friends. I can sympathize at times. Meanwhile the advice from ChatGPT is good advice for making and maintaining connections in the DFIR community as well.

For when I can’t Find My gear (10)

Drilling into the Cached Locations and examining in World map view, we see a cluster of activity around the Neptune Mountaineering. (You’ll also be able to find that Chad connected to their Guest Wi-Fi when he was visiting the store.)
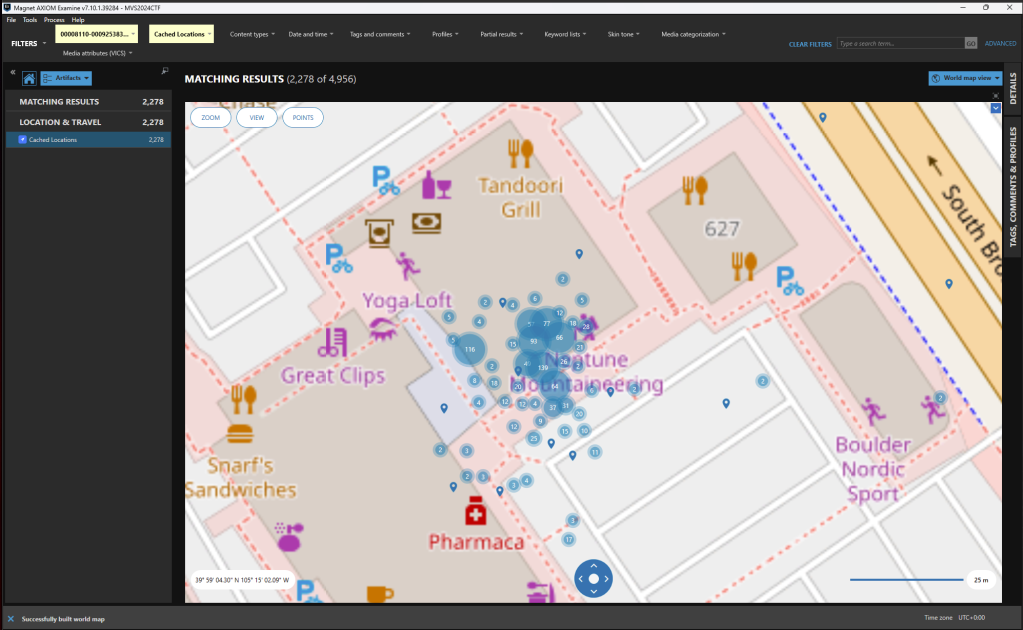
Just a couple steps away (10)

Apple Health Steps is one of the artifacts found under Connected Devices. If we apply a filter for just events on 12/3, we see four values recorded. Add the four together and you get the total steps for the day.

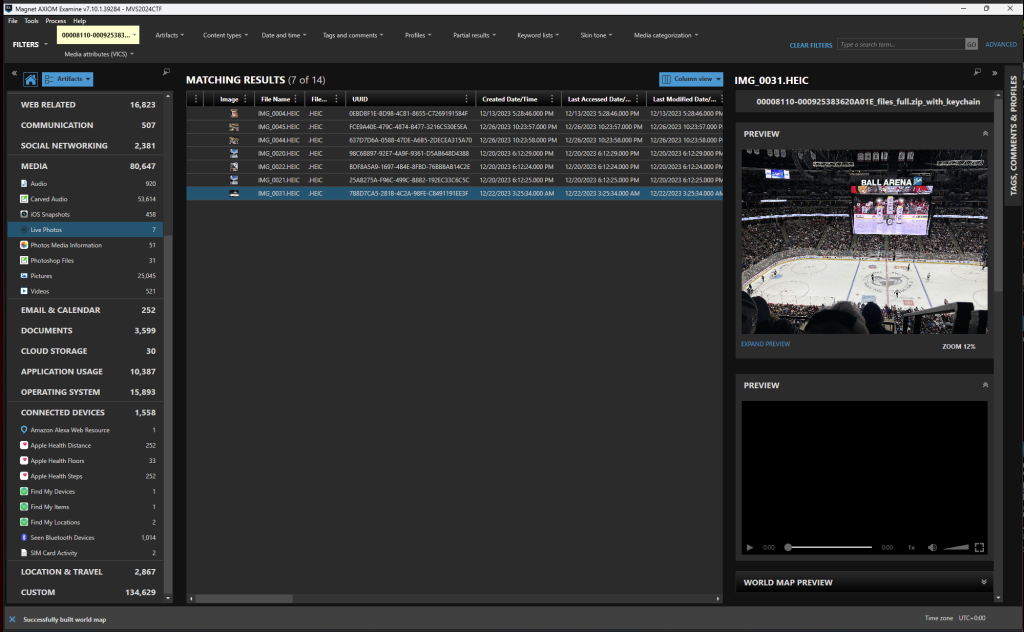
I hear Stanley cups are all the rage (25)

While perusing the photos I saw that there was one captured at a hockey game on December 22. In the image we can see that the game took place at the Ball Arena.
My sports knowledge is on par with my cooking abilities – not good. I decided to ‘phone a friend’ to help with this one, the Google Bard (now Gemini) AI.

Can anyone Kelp? (25)

If you filter out the applications from apple (com.apple…) there aren’t too many remaining, and of those only a few are games. Of those I can only see one dealing with greens.

The name of the application Terrarium was not accepted for an answer. Checking iLEAPP to see if there was another application that I had missed, I saw the full name of the game is Terrarium: Garden Idle. It’s a good idea to always validate your evidence with at least one addition tool from your primary.

The easy way or the hard way (25)

Again looking at the chat history we have a conversation between Chad an Rocco. The last message sent was on December 21, 2023 at 06:29:36 UTC.

Follow the Breadcrumbs (50)

This answer was easier to grab from iLEAPP as there’s a specific entry for Biome Text Input Sessions. Filtering for amazon, we see 4 entries. 2 of those occurred on December 24.

Season’s Greetings (75)

Start off with a search for Susan and we can see there’s a iMessage chat history. Chadwick’s first message to Susan says “Christmas Susan! 🪴 how have you been?”

MVS 2024 CTF: Ciphers
While working through the iOS questions I diverted my attention to a few of the Cipher questions when I needed to give my brain a change of pace. I only did a few of them.
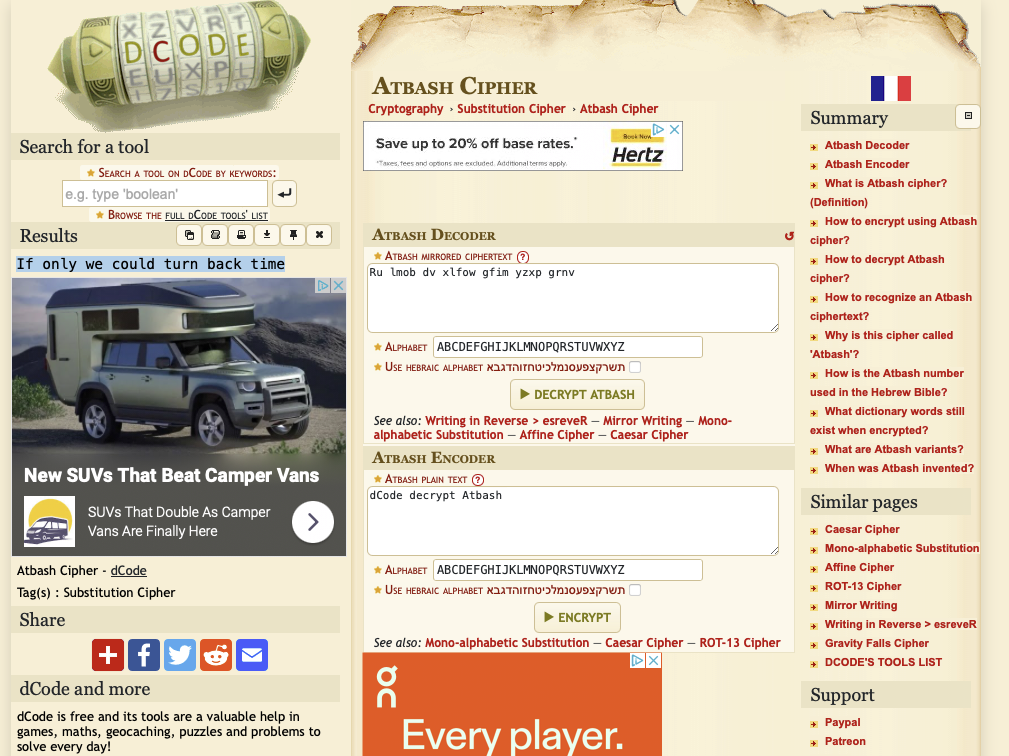
Have you ever tried reading the alphabet in reverse? (5)

For this one we’ll throw the sample text into dcode.fr. Doing so suggests it is an Atbash Cipher.
“Atbash (Mirror code), a substitution cipher replacing the first letter of the alphabet with the last, the second with the penultimate etc.”
That sounds to me like a backwards alphabet. Decode the text using the Atbash Cipher on dcode.fr.
Why did the bicycle fall over? It was tired of all the ROTation! (5)

From the clue we can be pretty sure this is a ROT cipher. Using CyberChef we can try the ROT13 Brute Force. Scanning through the output we see that the output for a rotation of 2 produces a legible result and is the answer for the challenge.

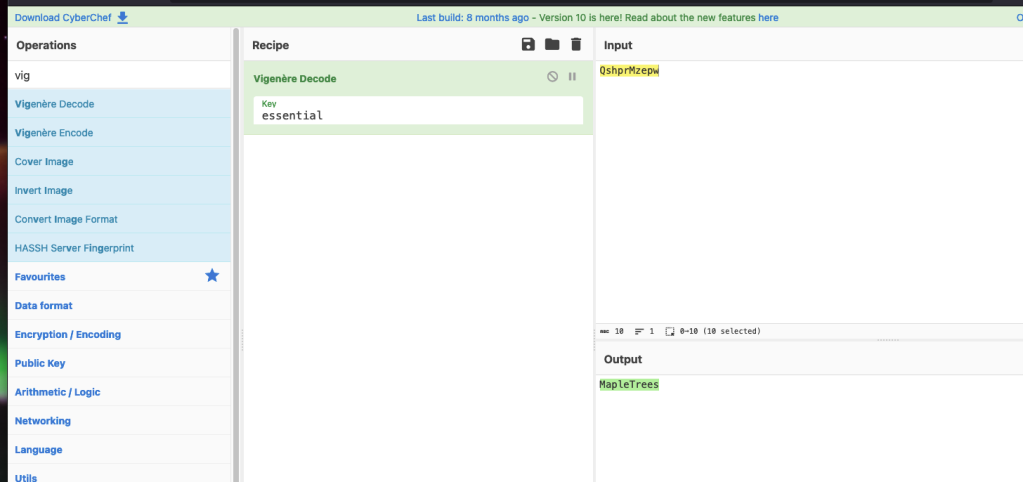
VIGorous ENcrypting? Embrace the Riddle’s Essence, it’s “essential”! (10)

A quick Googling on VIG and cipher and we learn there’s a Vigenère cipher.

Off to CyberChef. Choose the Vigenère cipher recipe, enter the input provided in the question, QshprMzepw, and use the key “essential”. The decoded text is MapleTrees.
That’s all for me. Thanks to Jessica Hyde and her team at Hexordia and the students at Champlain College that put all the effort into coming up with the challenges. Also thanks to the winningest Kevin who took the year off from competition to join the CTF creation team.
As always it was a lot of fun, and I learned a couple things along the way.



























































