It’s been just over a week since MalChela was initially released and already here have been a number of updates.
mStrings
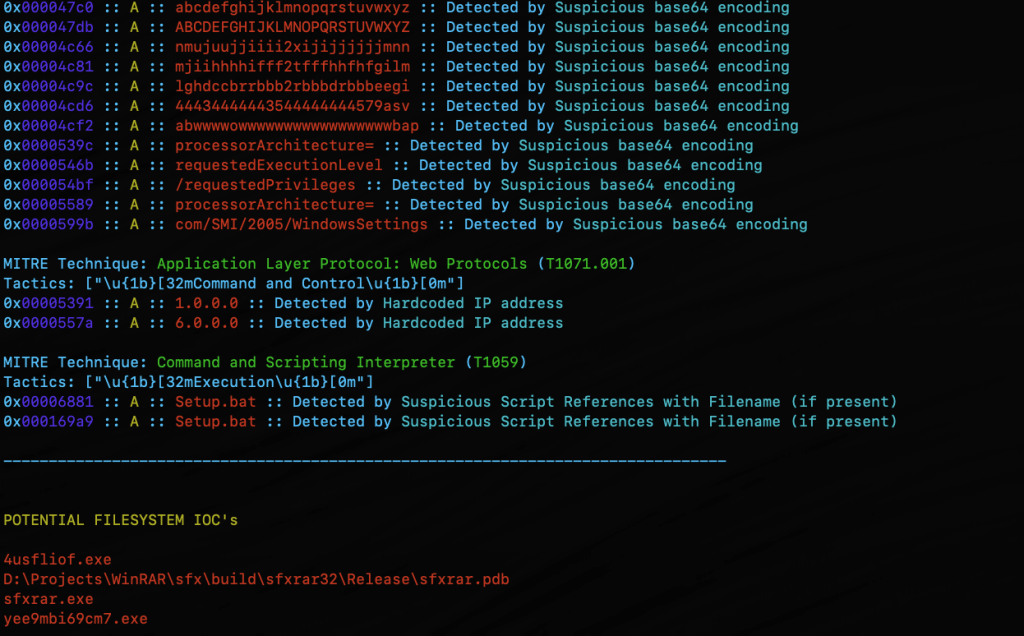
In the previous post, I walked through the new mStrings function. I think this is one of my favorites so far. It extracts strings from a file and uses Sigma rules defined in YAML against the strings to evaluate threats and align results to the MITRE ATT&CK framework.
For fun I pointed it at an old WannaCry sample . I had a proud papa moment at the positive network IOC detection.

Check for Updates
Next came a function to automatically check the GitHub repo for updates and encourage a git pull to grab the latest… because apparently I can’t stop myself and this project will just keep growing, as my sleep keeps dwindling. Personally I found it ironic that you have to update in order to get the update telling you that updates are available… but it will work for all future updates as they come. So go ahead and update why don’t you.

New File Analyzer module
Most recently a File Analyzer module has been added. Give it the path to your suspect file and it will return back:
- SHA-256 Hash
- Entropy (<7.5=high)
- A RegEx detection for packing (mileage may vary)
- PE Header info if it’s a PE
- File Metadata
- Yara Matches (any rules in yara_rules folder in workspace)
- If there’s a positive match for the hash on VirusTotal (leverages the same key as previously in MalChela with the Virus Total / Malware Bazaar lookup)
Lastly, you’re given the option of whether or not you want to run strings on the file, or return to the main menu.

I really like the idea of using this as a possible first step in static analysis. Run this first and opt for strings. Things look interesting there, throw it into mStrings. Positive match on VirusTotal – use the malware hash lookup and get a more detailed analysis. Use the results from mStrings to craft a YARA rule and add it to your repo for future detections.