It’s a strange but satisfying feeling to hit version 3.0, then realize soon after you’re already back in the weeds fixing, refining, and optimizing. That’s what this 3.0.1 release is all about — a tight round of updates aimed at boosting clarity and cutting noise, especially when running mStrings or working within the FileMiner panel. Additionally, a number of optimizations came about in getting MalChela to run smoothly on Toby, and to minimize any unnecessary re-building of the binaries. This post walks through what’s new and improved.
🧠 Smarter Detections in mStrings
The mstrings tool — one of the most feature-rich in the toolkit — got a round of refinements:
- Generic Executable detection removed: This was too noisy and matched a lot of clean files. It’s been replaced by more focused patterns.
- Suspicious DLLs now detected more precisely: Legit Windows DLLs like ole32.dll and gdiplus.dll are now excluded unless they’re paired with indicators like GetProcAddress, LoadLibrary, or manual syscall patterns.
- Rule cleanup and expansion: Several detections were removed, refined, or added (like packer stubs and dropper markers) to better target actual malicious behavior.
- Tighter MITRE mapping: Each detection is now carefully aligned to a corresponding MITRE ATT&CK technique, often down to the sub-technique level.
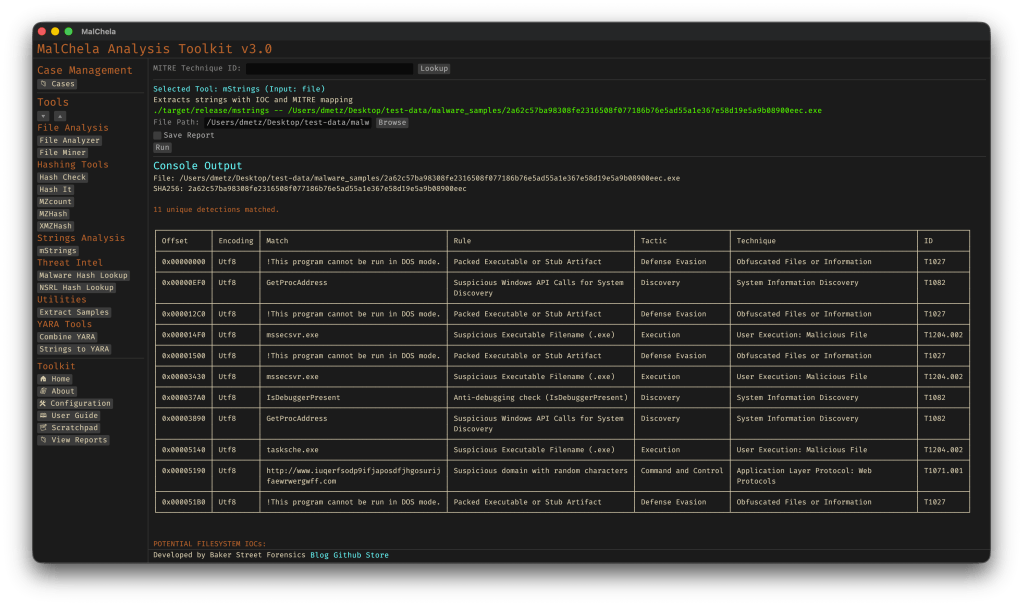
If you’ve ever run mstrings and felt unsure which hits mattered most — or got buried in generic noise — this update should feel much cleaner.
Reminder: You can easily update the detection criteria by modifying detections.yaml.
Have a detection to contribute to the project? Submit a pull request.
🔍 Built-In MITRE Lookup (GUI)
If a detection shows a MITRE ID like T1082, you can now look it up directly inside the GUI. The new MITRE Lookup Bar sits at the top of the config panel (only when running mstrings). Paste a technique ID, hit Lookup, and it’ll open the official MITRE ATT&CK page in your browser.
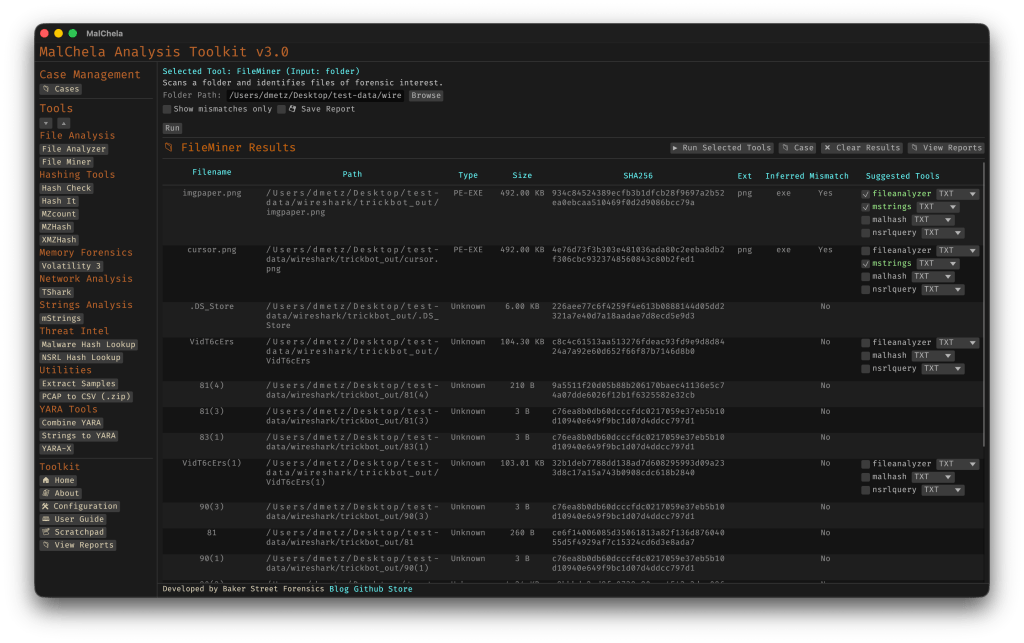
🗂️ FileMiner Improvements
The FileMiner GUI panel saw some polish too:
- “Select All” functionality: You can now batch-run tools across multiple matching files in a case — a huge time-saver during triage.

🧰 Build and Setup Updates
Two quick notes for folks cloning the repo for the first time:
- The release.sh script now builds all binaries in release mode — one command to build everything cleanly.
- Docs and README were updated to recommend building in –release mode from the start, especially for smoother GUI usage.
🧪 Platform Testing
Confirmed functional on:
- macOS (Silicon)
- Ubuntu (Desktop and minimal)
- REMnux (custom REMnux tools.yaml)
- Raspberry Pi (Zero 2W and 4B)
- Windows via WSL (CLI)
Still some quirks with native Windows support due to YARA compatibility and pathing, but if you’re a Windows power user and want to pitch in, I’d love your help.
💭 Final Thoughts
MalChela isn’t trying to replace your favorite tools — it’s trying to bundle them in ways that save time, reveal context, and give you clarity during analysis. The 3.0.1 release doesn’t bring sweeping new features, but it does make the experience tighter, more predictable, and more useful where it counts.
As always, thanks to those who’ve tested it, given feedback, or just watched quietly from the shadows. 🕵️♂️ If you want to contribute — whether it’s rules, regex, docs, or bugs — you’ll find me at dwmetz/MalChela.
Happy hunting.